The structure of a MySQL Backend can be designed however the administrator thinks is logical. There are few hard rules for how the structure has to be designed.
Front End/ Back End
- With modern applications there is a “front” and “back” end. The Back End is the database and infrastructure that allows users to access data through a Front End which would be the web based interface or native application on their mobile device.
Database Servers
- Database servers are either physical or virtual servers with an operating system installed and then the database software installed on the OS.
- For the database to be accessed by a front end not only does the database need to be configured properly, but the OS needs to be configured for the proper firewall rules and permissions.
MySQL Schema
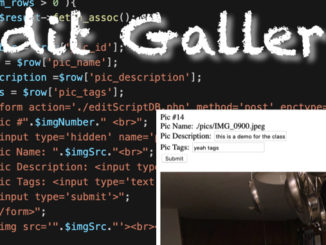
- Database – is the highest unit in a database system. You can have a single database for your company, or many. Having separate databases can be useful for security and reliability. Separate databases can be connected to by a single front end.
- Tables – contain the records in the database. Tables should store “like” data. Such as a Users Table, and a Parts Table.
- Columns Name – is the name of the data to be stored such as “firstName”.
- Primary Keys – Every record in a database table must be unique. A Primary Key is a unique entry for each record. generally the Primary Key column is setup to auto increment.
- Rows/ Records – Are the individual Records that are stored in a table
- Data Types – You assign a data type to the Column in a Table. Such as INT, TEXT, FLOAT. This means that an INT field will not accept “bob” as an entry.
- Schema – is the design and naming convention in the database. A front end can not store data to a database if the
Storage Engine
- DON’T TOUCH!!!
- Storage Engines are the component of MySQL that actually does the inserting and sorting actions. There can be reasons to change the Engine, but generally just leave it as the default which is currently InnoDB.
Users
- Databases have user accounts and permissions like other software. You can secure your database by having front ends access the database with only user accounts with the specific permissions that are required.

Be the first to comment