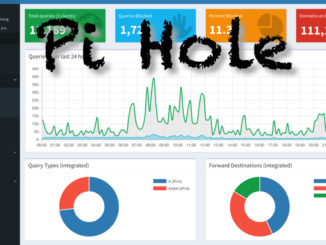
Raspberry Pi – Setup Pi Hole for DNS Security
The Pi Hole software allows you to turn your Raspberry Pi into a DNS Security device. After setup your client systems can use the Pi Hole as their DNS server, when websites try to resolve […]

The Pi Hole software allows you to turn your Raspberry Pi into a DNS Security device. After setup your client systems can use the Pi Hole as their DNS server, when websites try to resolve […]

UFW is a simple firewall application that is included with Ubuntu nd can be installed on other distributions of Linux. Note: For the demonstrations to work you may need to change settings or hardware configurations […]

Linux Permissions are much more simple than what is provided in Windows Active Directory. You have 3 permission types that you can apply to 3 groups. The permissions are Read, Write and Execute which can […]
Managing Groups in Linux is relatively simple. It’s important to realize Linux users, groups and permissions are much simpler than in Windows Server. Group Configuration File sudo vim /etc/group – opens Group configuration file in […]
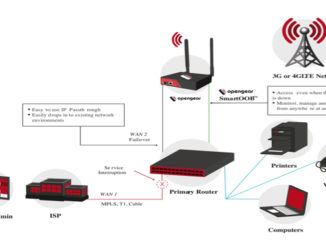
Out of Band Management is the ability to access your network equipment remotely using a network connection other than the main one used by your organization. You can use Out of Band Management equipment to […]
Doxxing is when personal information is released about people online. More than the act of doxxing itself, the more damaging component is the call to actions that accompany doxxing.